TEE Private Proving
The Succinct Prover Network supports fast proof generation on GPUs without revealing the encrypted proof inputs to any third party (including Succinct) through Trusted Execution Environments (TEEs). It is currently powered by the Phala Cloud solution.
How It Works
When enabling TEE Private Proving, the proof requests are not sent to the Succinct Private Network infra, but instead to a TEE application (hosted at tee.sp1-lumiere.xyz). The tee.sp1-lumiere.xyz TLS certificates are managed by the TEE application itself, allowing encrypted proof inputs to remain private.
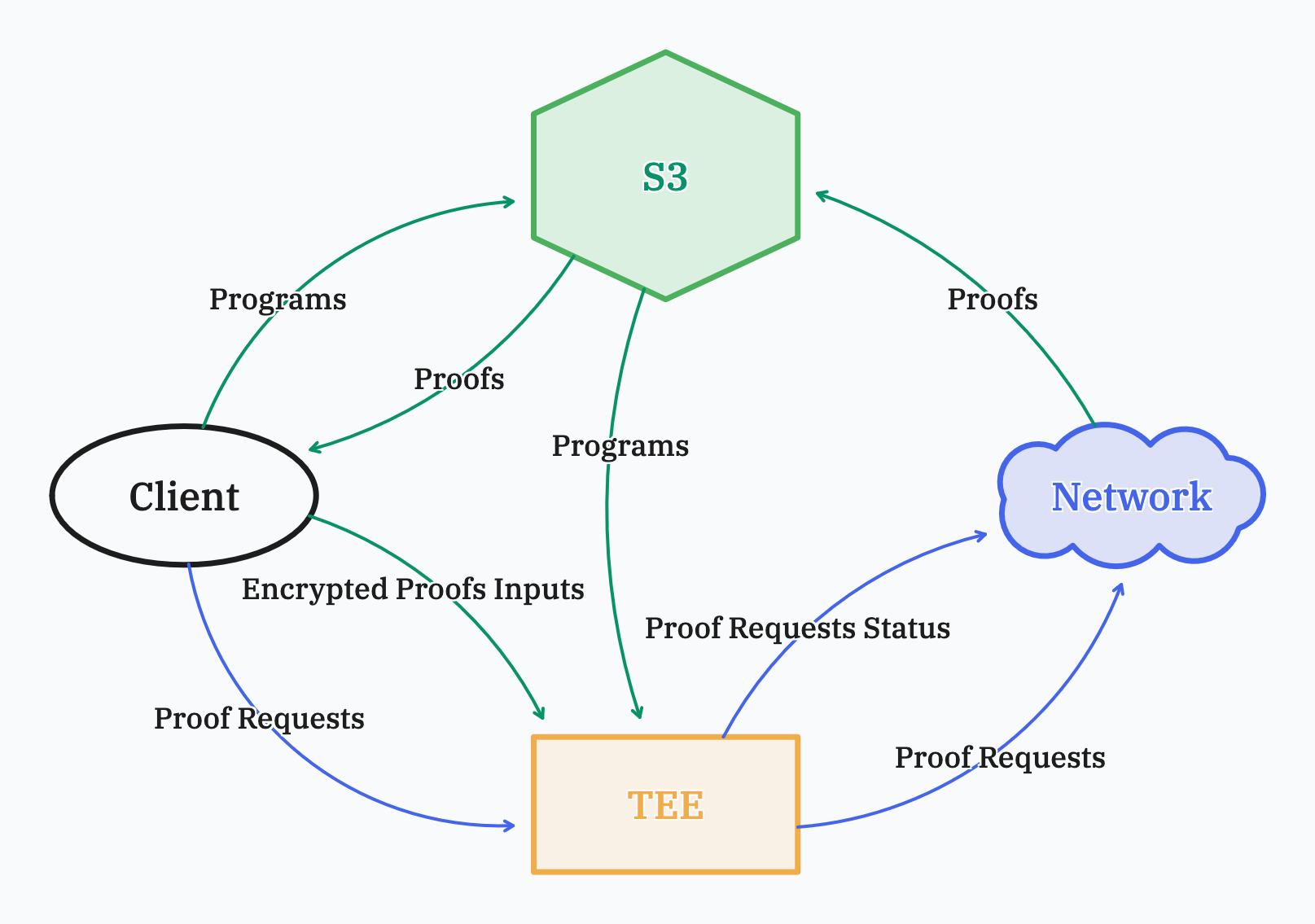
The workflow is the following:
- The client app create a proof request using the SP1 SDK.
- The proof request is sent to the TEE, and is proxied to the Network
- A presigned URL is sent to the client to store the program in S3
- Another presigned URL is sent to the client to store the encrypted proof inputs in the TEE
- The proof is generated inside the TEE
- The program is downloaded from S3
- The encrypted proof inputs are already in the TEE
- The program is first executed, and then the proof is generated
- When the proof is generated, The TEE updates the proof request status on the Network
- The proof is sent to the Network that store it to S3
- Meanwhile, the client app sends requests to the TEE, querying the proof request status
- The status requests are proxied to the Network
- When the proof request is fulfilled, the proof is downloaded from S3 and provided to the user
We can see from the workflow above that the encrypted proof inputs are directly sent to the TEE, keeping them private. Also, the proof is generated inside the TEE.
Usage
Currently, TEE Private Proving is in private beta and is only available through the Enterprise offering of the Succinct Prover Network. Contact us if you would like to try it.
Using TEE Private Proving in your application requires minimal changes. You just need to add the private() call to NetworkProverBuilder:
use sp1_sdk::{Prover, ProverClient};
// Initialize the prover using the network.
let client = ProverClient::builder()
.network()
.private() // enable private proving
.build()
.await;
// Setup your program.
let (pk, vk) = client.setup(ELF).await;
// Generate a proof.
let proof = client
.prove(&pk, &stdin)
.plonk()
.await
.unwrap();
TLS Certificates Verification
In order to ensure the communications to the TEE enclaves are secure, the tee.sp1-lumiere.xyz domain certificates must be managed by the TEE application itself. This is achieved by the Phala Zero Trust TLS protocol.
Phala provides mechanisms for anyone to verify and attest that the domain is managed by the TEE application. The process is described in the Domain Attestation section in the Phala Cloud documentation, and dstack-verifier, a tool to automate certificate verification is provided.
When all verifications pass, you’ve proven that only this specific TEE instance has the private key for the TLS certificate, and that the CAA DNS records prevent anyone else (even with domain access) from issuing certificates.
Application Integrity Verification
Phala also provides mechanisms for anyone to verify that an application is running inside a genuine, secure TEE with the expected configuration and code. You can follow the steps in the Application Integrity Verification section in the SP1-TEE Private Proving repository to verify the code running at tee.sp1-lumiere.xyz is expected.